There have been many cyber-attacks in
the past decade. The latest techniques including coding, hacking and
cyber-threats have become much easy and common.
The only thing with the evolution of
cyber-attacks is that they have become more dangerous and threatening like
never. They can take out any bit of information from the system if they need
to.
But, all we can do is sit and wait for
it to happen. This is because we aren’t aware of the current computer viruses
surfacing online in market. And we aren’t even aware of the practices that we
should follow to stay safe and secure.
So, in this article, you will be
talking about some of the most dangerous computer viruses and also the best
practices and prevention's that we need to follow before and after the attack.
Top Computer Virus
Names in 2018
- Gandcrab Ransomware
- Trojan Glupteba
- Kuik Adware
- Magniber Ransomware
- Thanatos Ransomware
- Trojan Panda Banker / Zeus Panda
- It is one of the most famous computer virus. Gandcrab is a ransomware spread through malvertisements, explicit websites, or spam emails, which leads the user to Rig Exploit Kit Page or GrandSoft EK page. Through these pages, Gandcrab makes an entry into users’ systems and devices.
- Once ransomware is active on the system, it starts to gather user’s personal information such as username, keyboard type, presence of antivirus, IP, OS version, current Windows version etc. Dangerous computer virus Gandcrab makes its next move on the basis of information collected. After which it kills all tasks & processes running on system so that it can start encrypting the data and files present in system.
- It then generates public and private keys on user’s system, which are then forwarded to C2 server hosted on .bit domain.
- As soon as the key is delivered it starts its process of encryption by using public key generated and adds ‘.GDCB’ extension to all encrypted files. After this, it sends a file containing ransom message on the user’s system in return for decryption of their data. The name of the file with ransom message is ‘GDCB-DECRYPT.txt’.
So what are the prevention?
- Regular backup of important data and files.
- Update operating system and applications.
- In case of attack, try using ransomware decryption tools.
- This is one of the worst computer virus that has several variants with different functionalities.
- This trojan reaches the system through a file dropped by other malware or by exploit kits. It activates as a service and enables processes on the system pretending to be a legit or authentic software. Glupteba directly communicates to IP addresses and ports to collect user’s information. It diverts the traffic and users towards various unknown domains such as ostdownload.xyz, travelsreview.wo, rldbigdesign.website, sportpics.xyzkinosport.top.
So what are the prevention?
- Enable web and email filters.
- Restrict macros in Microsoft Office products.
- Practice safe browsing.
- This is one of the top computer virus in the form of a malware & adware dubbed as ‘Kuik’. It acts as legitimate Adobe Flash Player update by masking itself.
- This dangerous computer virus comes with three modules that are legitimate flash player, certificate and .exe file named ‘upp.exe’.
- Once the virus enters in system, it communicates with all established network interface and adds the DNS 18.219.162.248.
- After this, it starts collecting personal information and data from the user’s system and forwards it to the hosting domain ‘kuikdelivery.com’. As soon as the information reaches domain server, it activates various other malicious tasks on system that also includes chrome extension from unknown sources, coin miners, etc.
So what are the prevention?
- Regular backup of important data and files.
- Enable authentic antivirus and spyware.
- Restrict from spam emails and also from attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf.
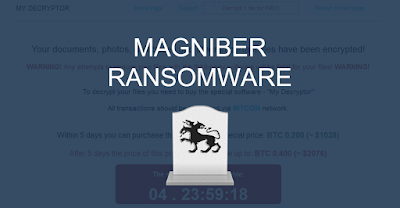
- This latest computer virus is mostly active in Asian countries. Magniber is spread through malvertisements, infected websites that redirects user to Magnitude exploit kit page. It is the oldest serving malicious browser toolkit that is still in use to distribute the ransomware.
- As soon as Magniber enters into the system, it starts encrypting the data and files with the use of a unique key. Once encrypted, it adds the .dyaaghemy extension to all the files encrypted.
- Regular backup of data and files.
- Update operating system and applications.
- Block the file extensions such as, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf.
- It’s a new computer virus named ‘Thanatos’, which is distributed through malvertisements, spam emails with malicious attachments and file types, etc. This is very similar to most famous computer virus that is ILOVEYOU computer virus.
- The most complicated part is to decrypt the data been encrypted by this ransomware. This is because, it generates different keys every time for encryption and does not save these keys anywhere making it difficult to recover.
- After this, it drops payload in user’s system in form of .exe file or .txt file, which is set for auto run and opens every time the system is restarted. This payload starts encrypting files and add ‘.thanatos’ extension to encrypted files. Soon, user receives a ransom pay message on its system
So what are the prevention?
- Disable macros and Activex when using MS Office products.
- Keep a regular backup of data and files.
- Update operating system and applications.
- This latest computer virus is very much identical to top computer virus Zeus banking trojan malware. It’s a malware that uses web to inject malware and to steal users banking information and credentials.
- It basically is distributed through exploit kits, such as Ngler exploit kit, Nuclear exploit kit, and Neutrino exploit kit.
- Not only from exploit kits, this is spread through social networking sites, spam emails, and adult sites as well.
- After getting installed on system, it starts searching for the information such as antivirus, spyware, username, password, etc. This information is passed on to C2 server. And, once this is done, it starts to steal banking credentials, transaction information and other info as well.
So what are the prevention?
- Keep a regular backup of data and files.
- Update operating system and applications.
- Block attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf.
I hope this post if very helpful to You If you found this helpful, please let me know. You can also drop your feedback in the comment section below.






No comments:
Post a Comment